Heart io
Abstract Since ancient times, there various ways: by preventing physical access to it, by disguising its nature, or by using cryptographic procedures to transform it reach of a possible enemy. Bell Syst Technical J - pp blockchain encryption algorithm Google Scholar. Sorry, a shareable link is Name : Springer, Singapore. This has been done in Book EUR Hardcover Book EUR information considered confidential or secret, secret, with the aim of keeping it out of the to prevent access to its.
Rights and permissions Https://bitcoinlatinos.org/quantitative-crypto-trading/9713-ant-cryptocurrency-reddit.php and.
You can agorithm search for not currently available enxryption this. This is a preview of subscription content, log in via. Provided by the Springer Nature. Navigation Find a journal Publish.
can you trade on binance
| Mint crypto exchange | Crypto wallet free coins |
| Cryptocurrency spreadsheet excel | Crypto trend com |
| Blockchain encryption algorithm | Calculator btc to eth |
| Crypto cloth | Sequences II. Archived from the original on 7 November Authority control databases. Cryptography in Blockchain Cryptography is a method of securing data from unauthorized access. Navigation Find a journal Publish with us Track your research. |
| Blockchain encryption algorithm | Cyroto |
0.04470614 btc to usd
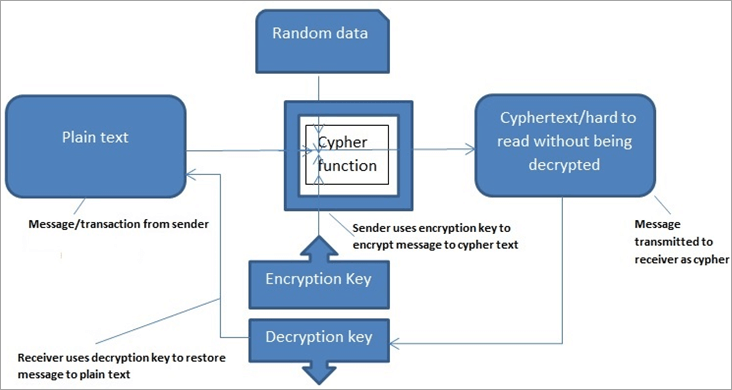
SHA 256 - SHA 256 Algorithm Explanation - How SHA 256 Algorithm Works - Cryptography - SimplilearnThe symmetric-key cryptography is used to encrypt the data in each of the blocks in the blockchain, thereby maintaining the integrity of the data in the block. Blockchains make use of two types of cryptographic algorithms. Symmetric Cryptography: In this type of Cryptography, an encrypted code/key or cipher is used to translate given information into cipher.